In all versions of Windows since the release of Windows Vista, one of the key features the Windows Start Menu supports is a quick search. You can try this by clicking on the start button and start typing. Typing when the Start Menu UI is active will change the screen to a search type screen. This is a great feature if you’re not sure where a program or document is located on your PC. While not an obvious UI element, understanding you can start typing while the Start Menu is active is a very handy feature to quickly find things.
We have seen many instances where users complain the search function cannot find anything. Search UI opens up, but searching does not find anything. We’ve seen this occur on Windows 10 workstations and Windows Server 2016 systems, but not necessarily on all systems. Additionally, we have seen a few isolated instances where at first the keyboard didn’t seem to work when logging into Office 365 with Modern Authentication enabled.
The core issue is CTFMON is not running. You can test this quickly by going to Run… on the Start Menu and starting up CTFMON manually. At this point, test to see if this clears up the Search issue. If so, this will stay running until you next reboot your system.
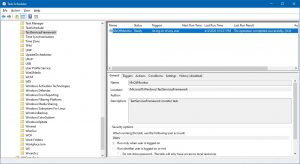
For a permanent fix, you will want to start Windows Task Scheduler and check to ensure the MsCtfMonitor is set to run automatically for any user who logs on. Launch the Task Scheduler application which is built into Windows and expand the tree on the left under Microsoft –> Windows –> TextServicesFramework. Check the task MsCtfMonitor to ensure it is not disabled. It should be set to Ready as the example below shows.
As we have been upgrading workstations and servers over the past couple of years, one of the things we might overlook in the upgrade plans is the impact on network devices. Some of these network devices have been in use for many years. Like Windows 7 they worked great and are not giving any outward signs of problems. With the move to updated operating systems (OS) from Microsoft, problems may occur trying to connect to these older devices.
A common problem we experience is with scanning to a network share on a new Windows server or workstation from an older copier. The copier may have been able to do this with the previous Microsoft OS (running Windows 7 or Windows Server 2008), but with the new OS (Windows 10 or Windows Server 2016+), it does not work.
The root cause is commonly caused by Microsoft deprecating (and removing) Server Message Block v1 (SMBv1) from Windows servers and workstations starting in late 2017. All versions of Windows since 2006 include the more updated (and more secure) versions of SMBv2. SMBv1 goes back to the early days of Windows and several security issues / problems have come to light since then. Windows XP and Server 2003 were the last versions of Windows that required SMBv1 to function and those went out of support in 2013 and 2014 respectively. Since 2017, SMBv1 has been removed with upgrades and updates. This removal can cause connectivity issues with devices that only support SMBv1.
There are two options in order of priority:
The above described issues to not impact these copiers from scanning to an email mailbox. Scanning to email has it’s own challenges, but SMBv1 is not used in that communications process.
As the COVID-19 crisis wears on, the number of folks looking to cash in by stealing data from unsuspecting internet users continues to grow. Last week, the FBI issued an alert warning citizens of crisis-related fake emails. These frequently claim to be from the CDC, WHO, or other healthcare organizations, allegedly sharing health information about the virus. They often contain malicious attachments or links which should be avoided and deleted expeditiously. Others claim to be from the government, and ask users to confirm personal details so that they can receive their stimulus checks. Requests for charity contributions, offers of airline refunds, fake cures, “vaccines,” and even fake test kits have all been used to prey on users who are more stressed, more vulnerable, and frequently working from home equipment that is less closely managed by an IT company.
Stealing Data – According to a recent article in Forbes:
A report from cybersecurity company Recorded Future noted a significant rise in website registrations related to the COVID-19 virus, some of which it believes are being used to either pilfer information from recipients or infect them with malware.
Lindsay Kaye, director of operation outcomes at Recorded Future, specifically called out the following domains as potentially dangerous:
coronavirusstatus[.]space
coronavirus-map[.]com
blogcoronacl.canalcero[.]digital
coronavirus[.]zone
coronavirus-realtime[.]com
coronavirus[.]app
bgvfr.coronavirusaware[.]xyz
coronavirusaware[.]xyz
It should go without saying, but is strongly recommended that you avoid visiting any sites associated with these domains. If you receive email correspondence with links to any of these, delete it immediately. In fact, during this time of heightened risk and susceptibility, you and your staff should be doubly suspicious about any correspondence from people or organizations with which they are not familiar. Cybercriminals and even state-sponsored hackers are using the elevated level of fear to improve the effectiveness of their phishing attempts.
An email titled “ALERT – COVID-19 CASES IN YOUR AREA” or similar could be all it takes to convince them to click a malicious link. A single misstep could lead to harmful software infecting their machine and their network. This initial compromise could eventually put sensitive or even mission critical data at risk. Even with security measures like VPNs in place, if the malicious software can log keystrokes, it can collect usernames and passwords. Criminals can use these to gain access to your networks, your inbox and contacts, or even access banking websites.
Users need advice, guidance, and training to help make ALL of the parts of your network more secure. Make sure your remote staff are aware that they are always at risk – and encourage them to BE SUSPICIOUS.
Stay safe and be well.